10 hours of SQL Server under attack – takeaways
Have you ever wondered what are signs of attacks on SQL Server?
Once in a while, just for fun, I do expose a SQL Server directly to the internet. Then I wait and see how long it takes for the attempts to breach happen.
This year at the SQLSaturday New York City conference which took place at the Microsoft offices in New York City, I had the honor to deliver my Performance Monitoring workshop as a 1 day PreCon . What distinguishes my workshop is that attendees can connect to my SQL Server, which is running a production-like workload, and do some hands-on analysis themselves.\
I decided to make it easy – for myself as well as for attackers – and left the standard SQL Server port 1433 exposed to the internet, on purpose.
Then I waited for the first break-in attempts to show up in the Logs.
In this post, I am sharing with you what happened:
First break-in attempts after 10 minutes
It took only 10 minutes, while I was still preparing the Demo-environment (workload simulations etc.) for the first attacker to try.

The attacker apparently came from Iran. – Yes, I know, this can be forged, but based on experience, this was likely not the case.
Who leaves SQL Server exposed to the public internet?
If you think it is unrealistic that someone would leave SQL Server exposed to the internet, I understand where you are coming from. However, not every company has sufficiently well-informed DBA’s and Network Admins working for them.
Shodan has a list of network scan results for the whole internet, and currently there are about 330.000 such SQL Server instances found as you can see here: https://www.shodan.io/search?query=SQL+Server (I exclude the number of browser services as those may well point to the same SQL Servers already in the list)
Main workshop day, waiting for the first attacker of the day
Then came the day of the workshop. This time, the SQL Server would be online and hence exposed much longer.
Just for fun, I made a bet with the attendees: which of the major nation-states known for aggressive and organized cyberattacks — China, russia, Iran, or North Korea — would be the first to hit my server that day?
Well, the first attempt to breach the sa account came from Saudi Arabia. 🙂 And in addition to that, for the remainder of that day, most attackers used North American IPs. Therefore, nobody won the bet.
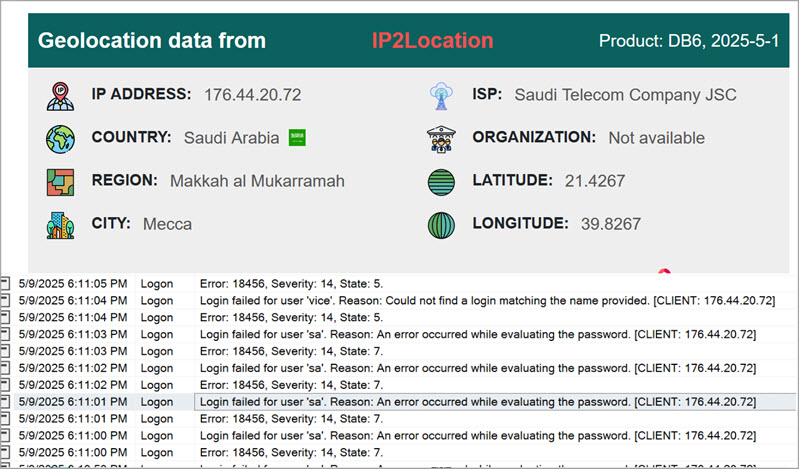
Security recommendation
Since sa is well documented for SQL Server, this is always the first account that is tried. Therefore, the recommendation is: do not use the sa account. Disable the sa account after setting a very long (100+ characters) password. Use a separate account for sysadmin-privileges.
Other signs of ongoing probing or attacks
So far, we have seen the classic attempts to breach the sa account followed by attempts of other well-known account names such as “admin”, “mssql”, “su” etc.
But there are other signs that someone is probing your environment and SQL Server.
Here are some of the typical error messages you will see in such cases:
![]()
![]()
![]()
So do not dismiss those. If you see these, pay extra attention.
I hope this was interesting.
If you feel you need a professional to look at your data estate from a security angle, please reach out to me and my team.
Andreas



Leave a Reply
Want to join the discussion?Feel free to contribute!